| As the Bundeswehr and the BSI do pioneering work in quantum-secure encryption, they should support the German private sector in implementing it. Without practical cooperation, the defense industry and DAX companies will fail to transition in time. |
| German federal agencies should raise awareness in the private sector. Recent Chinese advances in challenging conventional encryption – as well as “harvest now, decrypt later” attacks – mean that now is the time to become quantum-resilient. |
| The messaging software used by the Bundeswehr and other German federal entities is not yet quantum resilient. These software applications should be transitioned to hybrid encryption approaches immediately. |
| As standardization has been key to propelling the quantum transition, Germany’s government and companies should double-down on it, especially in the cloud, messaging, email, and remote access software sectors. |
On October 1, 2024, Chancellor Olaf Scholz set out Germany’s ambition in quantum technologies. “Our goal is clear: to be global leader in quantum technologies,” he stated. While quantum technologies encompass quantum computing, communication, sensing, and encryption, this DGAP Policy Brief focuses on only one of these three branches – post-quantum cryptography, also known as post-quantum encryption. With the exception of one example, it does not deal with quantum communication, which is another way of securing networks.
In line with Scholz’s statement, Germany’s public sector is leading in the implementation of post-quantum cryptography in their networks. The Bundeswehr, for instance, has done groundbreaking work by deploying quantum encryption algorithms to secure its 13,000-kilometer fiber network across Germany. Similarly, Germany’s Federal Office for Information Security (BSI) has been a leader in co-developing standards for quantum-secure encryption. However, this is not enough.
If Germany wants to be a leader in quantum encryption, its private companies will have to step up their efforts. Currently, they are losing ground internationally. As this policy brief shows, Germany’s larger technology companies are behind in implementation – at least when it comes to post-quantum encryption. Software AG, United Internet AG, BWI, TeamViewer, and AnyDesk are far from having a public plan on deploying this technology. Only SAP has started to experiment with post-quantum encryption but has not gone beyond trials. As a 2023 study by the BSI and KPMG shows, German companies that are not primarily in the IT sector fare even worse.
- Scope of Our Research
-
Our research is based on an extensive review of publicly available information, including official documents, press releases, and public statements from selected companies. It relies exclusively on open-source data, meaning that any unpublished/undisclosed implementation of quantum cryptography is not reflected in our findings. While the research we conducted was as comprehensive as possible, we cannot rule out that some updates may have been overlooked or released after October 2024 when we completed our data compilation.
We included the major companies in key information and communication technology industries, while also aiming to provide for geographic diversity. We did not, however, include Chinese platform providers – whether in the context of the pre- or post-quantum-encryption age – because it is assumed that the data collection requirements of the Chinese state make these insecure from the outset. Any form of encryption is weakened and subverted by China. Yet, it is possible that we inadvertently omitted other major platforms. Any omissions of major players in the industries mentioned were not intended.
As it is likely that the first powerful quantum computer that could break traditional encryption standards does not yet exist, the threat appears far away. However, countries are already harvesting data now that they will decrypt later when quantum computers will be powerful enough to break encryption, probably in the 2030s. Yet, with current breakneck advances in technology among the United States, China, and countries in Europe, an encryption-breaking quantum computer could arrive sooner rather than later. Chinese researchers have been shown to be particularly advanced in developing approaches to breaking asymmetric encryption. As a result, there is less time to deploy post-quantum cryptography than business leaders may think.
While some companies remain sluggish, others have already drawn up serious plans on how to accomplish the transition to quantum resilience. Below, we first analyze the quantum transition that is, at least partially, already underway. Then, we provide practical recommendations on how Germany can not only navigate this transition but also fulfill the ambition to leadership set out by its government.
Summary of Findings
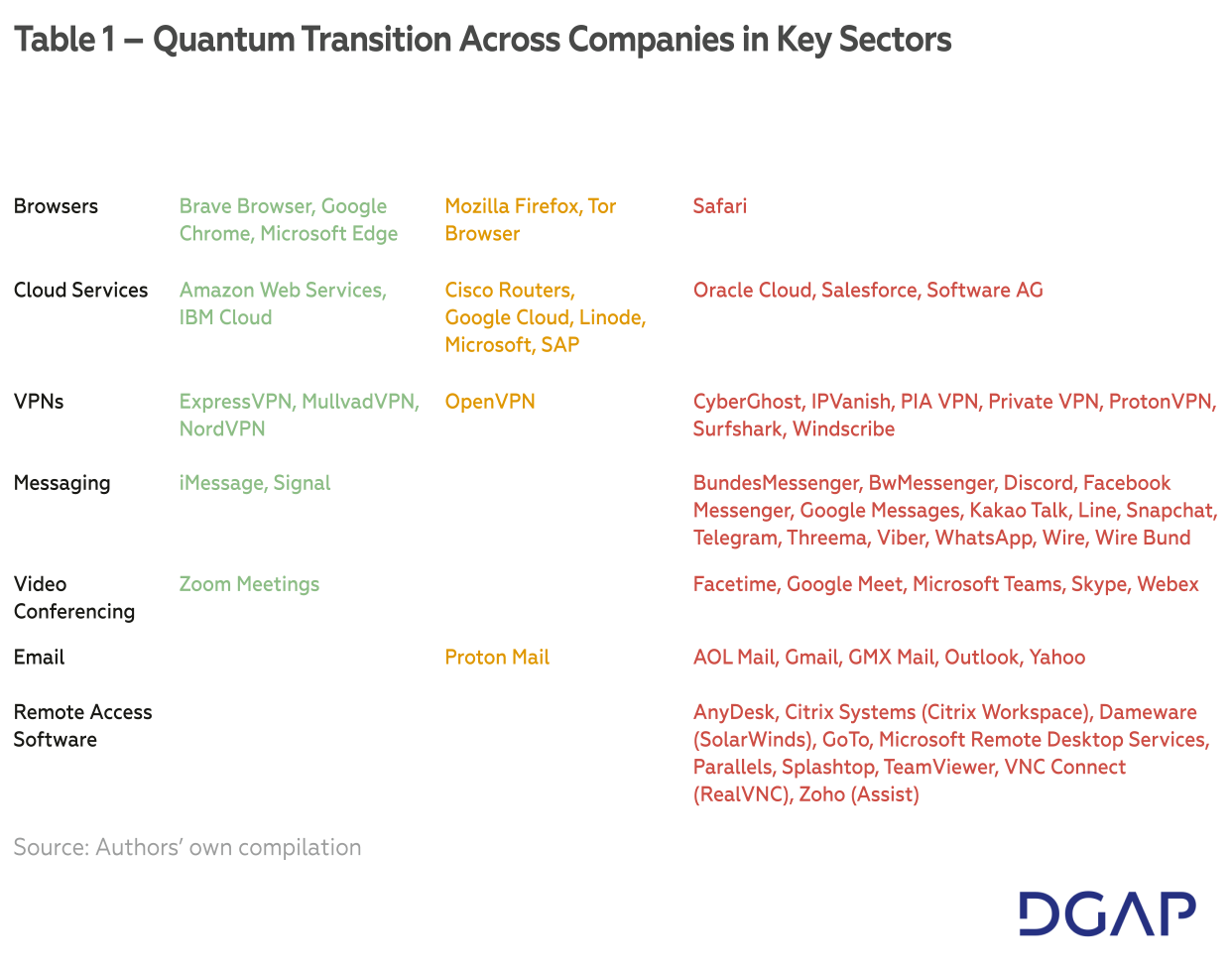
As summarized in Table 1, this paper provides an overview of the steps toward quantum resilience taken by major companies that hold a considerable market share in Germany and/or internationally in seven key sectors. We have grouped the companies’ progress into three main categories:
- Quantum Secure: encompasses products that have implemented post-quantum algorithms and/or updated existing protocols with quantum-secure cryptography. This categorization does not mean that these products are entirely quantum secure, but rather that they are closest to achieving this goal as compared to other products.
- Quantum Experimental: refers to companies that have already tested the deployment of quantum-secure encryption algorithms in their services or indicated that implementation is forthcoming.
- Quantum Insecure: indicates companies that have not publicly disclosed any efforts toward implementing quantum-secure encryption.
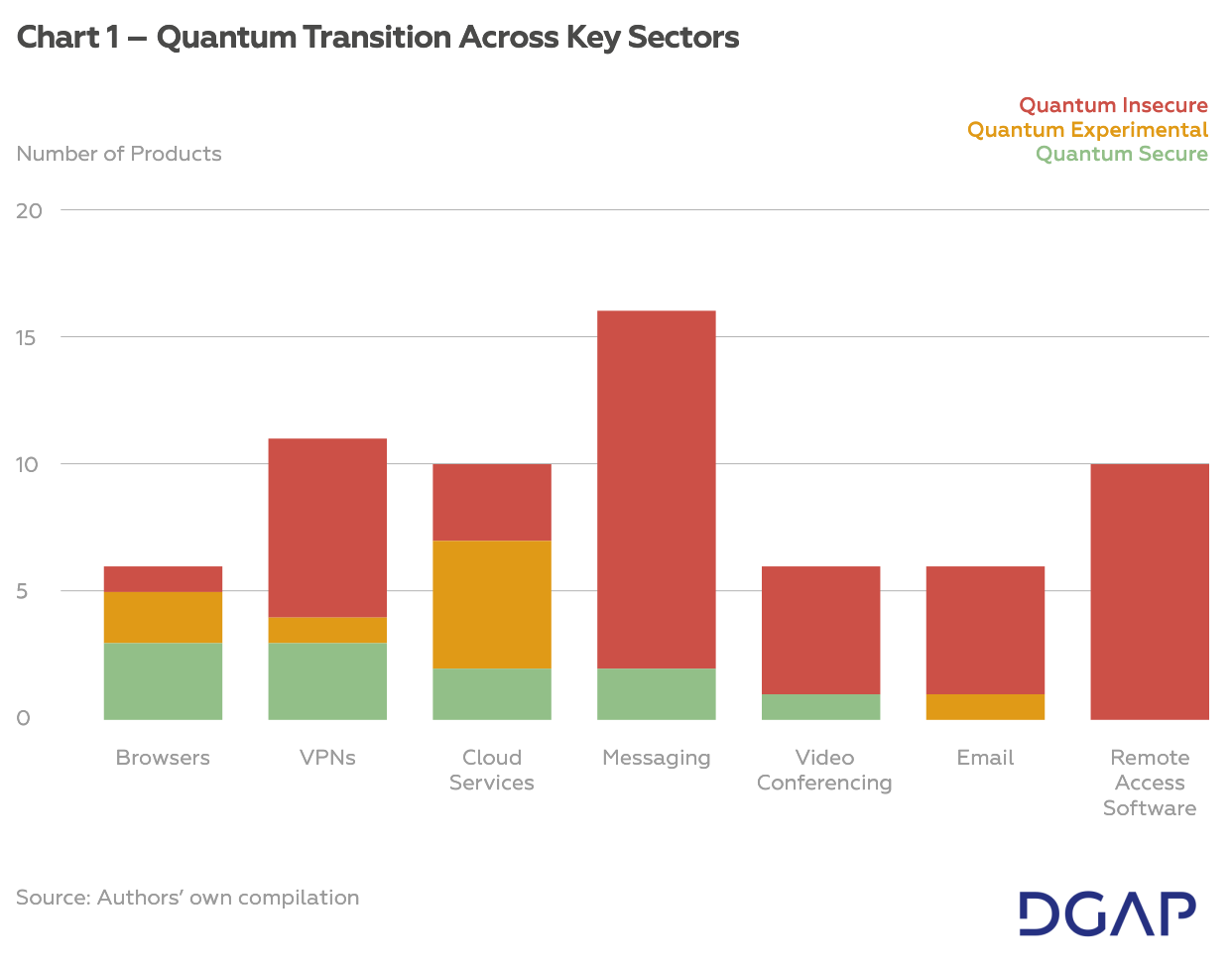
As illustrated in Chart 1, the leading industry in deploying quantum-safe encryption is browsers. Chrome, Brave, and Edge already have options to enable hybrid encryption, combining classical cryptographic algorithms with post-quantum cryptography algorithms. Firefox and Tor Browser are in the experimental stage, while Safari has not yet announced any advances in this regard.
Just as advanced are cloud services. IBM Cloud and Amazon Web Services (AWS) both have commercialized solutions, and many other providers – such as SAP, Microsoft, and Cisco – are actively working to deploy quantum-resilient encryption in their systems.
Providers of virtual private networks (VPNs) fare similarly. ExpressVPN, MullvadVPN, and NordVPN offer customers the ability for their traffic to become safe from quantum snooping and OpenVPN is being developed in this direction.
Regarding messaging services, there is a choice of two major messengers to choose from: Signal and iMessage. However, worryingly, no other messaging services appear to be deploying post-quantum encryption methods, let alone experimenting with them.
Video conferencing is already leaning to the other side of the spectrum. If users want a quantum-proof experience, they can only rely on Zoom as the market does not offer any alternatives. Microsoft Teams, Webex, and other major providers have failed to deploy quantum-proof encryption.
It is even worse when it comes to email or remote access software. Not a single email provider has yet to offer quantum-proof solutions. While Proton is the only email service provider that has explicitly discussed quantum resilience in a blogpost, it does not yet have any solutions. The remote access software industry is the worst performer. No company has even announced yet that it is experimenting with quantum encryption to secure their products, let alone deploying them.
Preparedness in Individual Sectors
Messaging
Quantum Secure: Of the messaging apps we examined, only two have already deployed post-quantum algorithms: Signal and iMessage. To accomplish this, Signal uses both the elliptic curve key agreement protocol X25519 (traditional cryptography) as well as the post-quantum cryptographic algorithm CRYSTALS-Kyber. This means that, in addition to its already existing layer of encryption that contains problems that are difficult for traditional computers to solve, Signal added a layer of encryption with problems that are very difficult for quantum computers to solve. Signal announced this deployment on September 19, 2023.
On February 21, 2024, Apple followed suit by proclaiming that it is taking a similar hybrid approach that adds quantum cryptography (Kyber1024) on top of traditional elliptic curve cryptography. Yet, Apple went even further than Signal by introducing post-quantum rekeying. This technology ensures that, even if an attacker managed to compromise a conversation at a certain point, the attacker would lose the ability to do so for new messages. In short, post-quantum rekeying offers yet another layer of security.
Quantum Insecure: Meanwhile, most – if not all – other messengers we examined do not deploy post-quantum cryptography. Those are BwMessenger, BundesMessenger, Wire Bund, WhatsApp, Facebook Messenger, Google Messages, Telegram, Viber, Line, Discord, Kakao Talk, Snapchat, Threema, and Wire.
Quantum Experimental: In a post on October 24, 2023, Proton stated that it had selected the CRYSTALS-Dilithium digital protocol for digital signatures, which verifies the sender’s identity, and CRYSTALS-Kyber, a post-quantum cryptography algorithm, for use in its encryption in combination with X25519 (traditional cryptography). However, these security features have yet to be deployed.
Quantum Insecure: All of the other email service providers that we looked at – Gmail, Outlook, Yahoo, AOL Mail, and GMX Mail – are unprepared and will likely remain so in the near future.
Video Conferencing
Quantum Secure: On May 24, 2024, Zoom announced that, from then on, Zoom Meetings would also be protected by Kyber768, which provides a bit less security than the Kyber1024 used by Apple. Like other companies, Zoom uses a hybrid approach that combines traditional and post-quantum cryptography to protect its services. Yet, Zoom Meetings does not use post-quantum cryptography by default. Users need to manually enable end-to-end-encryption to also use the quantum-proof algorithm.
Quantum Insecure: Worryingly for users, Zoom offers the only choice to have post-quantum resilient video conferencing. Skype, Webex, Microsoft Teams, Facetime, and Google Meet are all open to being compromised by a quantum computer or “harvest now, decrypt later” attacks.
Remote Access Software
Quantum Insecure: Remote access software is the sector that is the least prepared for quantum computer attacks. None of the major providers, e.g., TeamViewer, GoTo, AnyDesk, Microsoft (Remote Desktop Services), Citrix Systems (Citrix Workspace), VNC Connect (RealVNC), Splashtop, Zoho Assist, Dameware (SolarWinds), or Parallels, have declared that they are working on deploying post-quantum cryptography to protect their services.
Browsers
Quantum Secure: As of August 2023, Google Chrome deployed Kyber768 alongside the elliptic curve algorithm X25519 to establish symmetric keys in TLS, which is a networking protocol. While the symmetric encryption algorithms in TLS protect data in transit, the creation of symmetric keys is vulnerable. This is why Chrome transitioned to quantum-resistant session keys. Whenever browsers like Chrome establish a connection to a website or transmit a password, for instance, the connection is protected with TLS.
As Brave Browser and Microsoft Edge are based on Chromium, the open-source version of Chrome, they also include the TLS 1.3 “hybridized Kyber support” feature that Chrome has.
Quantum Experimental: In January 2024, Firefox Nightly, a development version of the browser, received an update that would allow it to support post-quantum key agreement. It might be rolled out to the standard version of Firefox soon.
In March 2023, a developer for the Tor Browser mentioned that it will transition to quantum-proof algorithms. The first step was to be implemented in 2023 by breaking up larger messages into smaller messages via a method called “fragmented cells.” This method would allow Tor Browser to implement quantum-resistant encryption in the future.
Quantum Insecure: While Apple has been cutting-edge in bringing post-quantum encryption to iMessage, it has been lagging when it comes to its SafariBrowser. Safari remains inherently vulnerable.
Cloud Services
Quantum Secure: In 2020, IBM Cloud became one of the earliest adopters of quantum-resistant algorithms that facilitate secure communications between clients and servers. Like many other companies, it relies on a hybrid approach in which Kyber512, Kyber768, and Kyber1024 ensure that key exchanges are done in a quantum-proof manner.
In June 2023, Amazon Web Services (AWS) stated that a variety of its services, including its AWS Key Management Service, AWS Certificate Manager, and AWS Secrets Manager TLS endpoints already deploy post-quantum-hybrid key exchange with Kyber.
Quantum Experimental: SAP has developed a few proofs of concept to test the feasibility of a quantum-resistant algorithm roll out, but it has not yet deployed any in its systems.
In September 2024, Microsoft proclaimed that it released support for post-quantum algorithms in its cryptographic library SymCrypt.
Cisco has developed the Secure Key Integration Protocol (SKIP), which allows Cisco devices to use quantum-secure keys provided by quantum key distribution systems (QKD).
Akamai Technology’s Linode has been testing open-source implementations of post-quantum algorithms, but it has not yet taken any major steps to deploy them on a wider scale.
Google Cloud is using the NTRU-HRSS-KEM algorithm instead of Kyber since the latter’s intellectual property status is still unclear. It is only using it for its internal communications, however, and has not deployed it more broadly for Google Cloud customers.
Quantum Insecure: The German company Software AG as well as the US-based companies Salesforce and Oracle Cloud have not yet shown any signs of experimenting with post-quantum encryption and are far from having it deployed.
Virtual Private Networks (VPNs)
Quantum Secure: On October 25, 2023, ExpressVPN proclaimed that it had added post-quantum resilience to its Lightway VPN protocol. It uses P256_KYBER_LEVEL1 for UDP and P521_KYBER_LEVEL5 for TCP. Both UDP and TCP are data transmission protocols, which are a set of rules that lay out how data is transmitted across devices.
For its part, MullvadVPN announced in August 2024 that it uses quantum-proof Classic McEliece and Kyber algorithms on its WireGuard servers.
At the end of September 2024, NordVPN launched a Linux app update that includes the first post-quantum cryptography upgrade for the Nordlynx protocol. It plans to extend this support to all its applications.
Quantum Experimental: Around 2020, Microsoft released a version of OpenVPN, Post-Quantum Crypto VPN, which integrates post-quantum cryptography into VPN software.
Quantum Insecure: While users can choose among a few companies that deploy post-quantum cryptography in their networks, a large portion of companies has been inactive on this front. Those are: Surfshark, PIA VPN, Private VPN, CyberGhost, Windscribe, IPVanish, and ProtonVPN.
Policy Recommendations for Germany
We have provided the above analysis to lay out where Germany currently stands in the transition to a quantum-resilient infrastructure that relies on post-quantum encryption. While Germany’s government sector proves to be slightly more advanced, its private sector is inherently vulnerable. On the other side of the Atlantic the picture is different. In the United States, a few companies have remarkably accelerated their efforts to become quantum secure. Yet, there too, many are still lagging and remain vulnerable to “harvest now, decrypt later” attacks. To begin to catch up to their international competition, German actors should take the following steps:
- Double down on standardization – Standardization appears to be the single most important factor for companies to accomplish the quantum transition. Most company transitions occurred after July 2022 when the US-based National Institute of Standards and Technology (NIST) chose and announced four quantum-resistant-cryptographic algorithms. In this context, efforts by the German Federal Office of Information Security (BSI) and email services provider Proton to establish a post-quantum public-key algorithm extension for the OpenPGP standard are laudable and should be doubled-down upon.
- Just do it – In the messaging industry, Signal and iMessage have shown that updating messaging protocols is possible. German products must follow their example and simply make the transition. Neither BWMessenger nor BundesMessenger is currently quantum secure. There is no reason why they should not be.
- Make it easy – When German companies enter the quantum transition, they need to avoid making quantum-proof services cumbersome to users. In MullvadVPN, users need to actively enable quantum-resistant tunnels. In the Chrome, Brave, and Edge browsers, quantum-proof features are still optional. Further, the level of risk when enabling these features is communicated too vaguely – Chrome, for example, warns users “you could…compromise your security or privacy” by doing so. This does not incentivize adoption. In Zoom, quantum-proof communications require enabling end-to-end encryption, leaving users with an all or nothing option. Instead, Zoom calls should be end-to-end encrypted by default with the option of activating post-quantum encryption.
- Increase transparency – Companies need to make clear where they stand in the quantum transition. SAP, for instance, states that it has developed proofs of concept, but it does not provide a timeline detailing when it will deploy its quantum-proof solutions. Others are claiming that only parts of their products are quantum-resilient. NordVPN’s quantum-update applies only to the Linux app; MullvadVPN’s only to their desktop app and not to iOS or Android. More explanation about why these choices were made would be helpful.
The authors would like to thank Heike Hagemeier for her insightful feedback on earlier drafts of this DGAP Policy Brief. Any errors are the sole responsibility of the authors.
To see the appendix of this Policy Brief – including a timeline of the transition to quantum encryption and a chart with headquarter locations of selected companies – please download the pdf here or by clicking on the link at the top right.